In most organizations, the Software Development Lifecycle (SDLC) is a well-oiled machine for developing, releasing, and maintaining software, geared towards meeting requirements in functionality and features, typically to fulfill a specific business objective. However, increasing concerns and business risks associated with insecure software have focused more attention on the need to integrate security into the development process. The typical SDLC process looks like this:
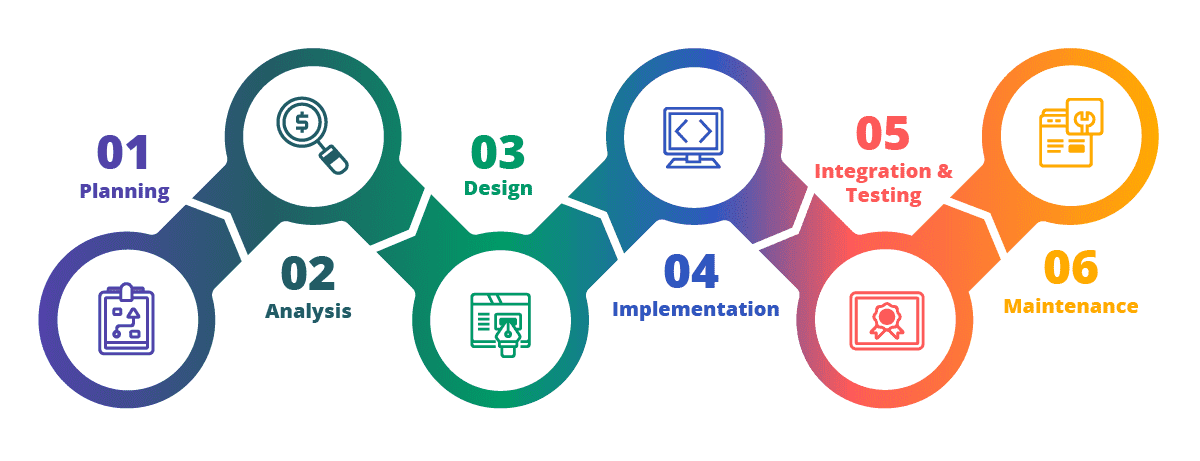
The idea is to have security built in, rather than bolted on, and to maintain the security paradigm during every phase so that the entire SDLC is secure.
Common practice has been to perform security-related activities only as part of the testing phase This post facto approach usually results in a high number of issues discovered too late. It is a far better practice to integrate activities across the SDLC to help discover and reduce vulnerabilities early, effectively building security in. A secure SDLC process means that security assurance activities such as penetration testing, code review, and architecture analysis are an integral part of development. Today we’d like to talk about penetration testing and when it makes sense to have it as part of SDLC.
Eliminate vulnerabilities in your server-side applications and APIs
Penetration testing mimics the steps a threat agent might take to exploit your vulnerabilities. It then demonstrates the impact and provides clear guidance to fix them.
Pentest is recommended for all systems that deal with customer sensitive data such as e-commerce, medicine—which uses the social security number—, banking systems, and so on.
Recently, Softjourn was involved in penetration testing of an access control service for one of our customers in the ticketing industry. In this case, the vulnerability found with the help of penetration testing was identity control: threat agents would have been able to get access to event, venue and entrance settings without having an admin login and access.
Another example Softjourn saw in the prepaid card service was session management. If an app stores login and password, it is possible to create a dump version of the app and gain access to user data.