As these technologies continue to evolve, financial institutions and fintechs are trying hard to include voice authentication in their services, allowing voices to act similarly to other biometrics, like fingerprint or facial recognition.
Voice Recognition Market Overview
According to a report by MarketsandMarkets, the global voice recognition market size was valued at $9.27 billion in 2020 and is projected to reach $27.16 billion by 2025, growing at a CAGR of 23% during the forecasted period.
"Voice biometrics has the potential to eliminate passwords altogether, making the customer experience more secure and seamless." - Brett Beranek, Vice President of Biometric Technology at Nuance Communications.
In 2022, there were around 142 million users of voice assistants in the US alone, according to Statista, which shows just how familiar people are becoming with this technology.
In a survey conducted by Pindrop, 60% of respondents reported using voice recognition technology at least once a month, with 77% using it on their smartphones. Voice authentication now includes a wide range of technologies that revolve around correctly responding to and recognizing a user’s voice. While using your voice to communicate with Alexa, Siri, and Google Assistant is straightforward, utilizing this technology for transaction authentication still has not reached its full potential.
How Does Voice Authentication Work?
Voice authentication is a biometric method that uniquely identifies users by measuring the distinctions in their voices, offering a secure alternative to traditional passwords. By analyzing over 70 parts involved in speech production, voice recognition technology digitizes speech to create a template or voice print that can later be used as a password.
The standard voice print consists of formants and dominant frequencies representing spoken word segments. After they've been recorded, these unique voice prints are securely stored in databases (like fingerprint and facial scans). Every time individuals recite a specific text or passphrase, they create a high-quality voice print, allowing the system to capture their unique vocal characteristics and recognize their voice in the future.
This process is similar to scanning all angles of a fingerprint on a touchpad. When the user subsequently utilizes the passphrase, specific words are compared with the stored voice print to authenticate their identity.
There are a few unique characteristics that must be highlighted when it comes to recognizing the uniqueness of one's voice: inflection, speech rate, clarity, brevity, and emotional mood.
Some voice authentication systems differ in that they do not rely on pre-recorded voice samples. Instead, they are trained to recognize similarities between individuals' voice patterns, enhancing the adaptability and flexibility of the technology. Here's how voice authentication works:
- Enrollment: The user first registers their voice by speaking a specific phrase multiple times. This helps the system understand and store the unique aspects of their voice.
- Feature Extraction: During authentication, the system captures the user's voice and extracts various features, such as pitch, tone, and cadence.
- Comparison: The extracted features are then compared to the stored voiceprint from the enrollment phase.
- Verification or Rejection: If there's a match, access is granted; otherwise, the authentication attempt is rejected.
Overall, voice authentication harnesses the distinct characteristics of an individual's voice, offering a robust and secure method for user identification and access control.

How Voice Authentication is Used
Voice recognition technology has rapidly expanded its applications with the advancement of AI, machine learning, and increased user acceptance. Here are several examples of voice recognition's diverse uses:
Biometric Verification: Voice authentication is considered a form of biometric verification, as it relies on unique physiological and behavioral characteristics of an individual's voice.
Security and Fraud Prevention: Voice authentication adds an extra layer of security to financial transactions by reducing the risk of identity theft, fraud, and unauthorized access. It helps ensure that only authorized individuals can access sensitive financial information or perform transactions.
Voiceprint Creation: To use voice authentication, users typically need to enroll by creating a voiceprint. This involves recording a sample of their voice, which is then converted into a unique digital representation based on specific voice characteristics.
Continuous Authentication: Voice authentication can also be used for continuous authentication during a conversation or interaction with a financial service provider. The system can monitor the ongoing conversation to ensure that the voice characteristics remain consistent and match the original voiceprint.
The wide-ranging adoption of voice recognition technology in finance showcases its versatility and practicality across various domains, enriching user experiences and facilitating efficient communication and control.
Since the technology has matured enough to become a standard in mobile phones, computers, and other devices, the financial sector realized the plethora of benefits the technology could bring in two distinct use cases: voice-driven customer service and voice-enabled payments.
According to a study by Opus Research, voice biometrics for authentication in the banking sector is expected to reach 1.9 billion users by 2023. That would be a significant rise from 69 million in 2016 as voice recognition technology in the meantime has made significant advancements in accuracy and has become widely available.
When we talk about the global voice recognition tech market reached close to 12 billion dollars in the US alone in 2022 and is projected to grow to up to 50 billion in the next decade. As technologies like voice assistants provide a very efficient way to do things, according to MarketsandMarkets, the conversational AI market in the USA is expected to reach $29.8 billion by 2028.

Voice-Driven Customer Service
Voice-driven customer service is focused on automated response systems. With chatbots, users are often stuck in endless loops of conversations that often do not help them solve a particular problem. That problem would be mitigated with voice technology as modern AI chatbots can mimic human intonation and understand speech patterns to make sound decisions.
Ana Botin, Executive Chairman of Santander Bank, stated, "We are already using voice biometrics for authentication and voice recognition to engage in more natural conversations with our customers. We believe that voice is the future for interacting with banking services."
Voice-driven customer service aims to provide a more convenient and seamless customer experience by eliminating the need for manual data entry or navigation through robust apps or complex websites. Users can execute transactions quickly and efficiently through natural language interactions and get all the information they need.
Garanti, a Turkish bank, has introduced a Mobile Interactive Assistant (MIA) within its mobile banking app, enabling customers to engage in voice-based interactions that simulate conversations with a real person.
MIA goes beyond standard functionality by informing customers about local promotions and discounts from nearby businesses. It possesses the capability to analyze user behavior, enabling it to anticipate and cater to their needs. MIA stands out for delivering an omnichannel experience, offering alternative solutions if a particular request cannot be addressed solely through the smartphone interface.
Voice-Based Payments
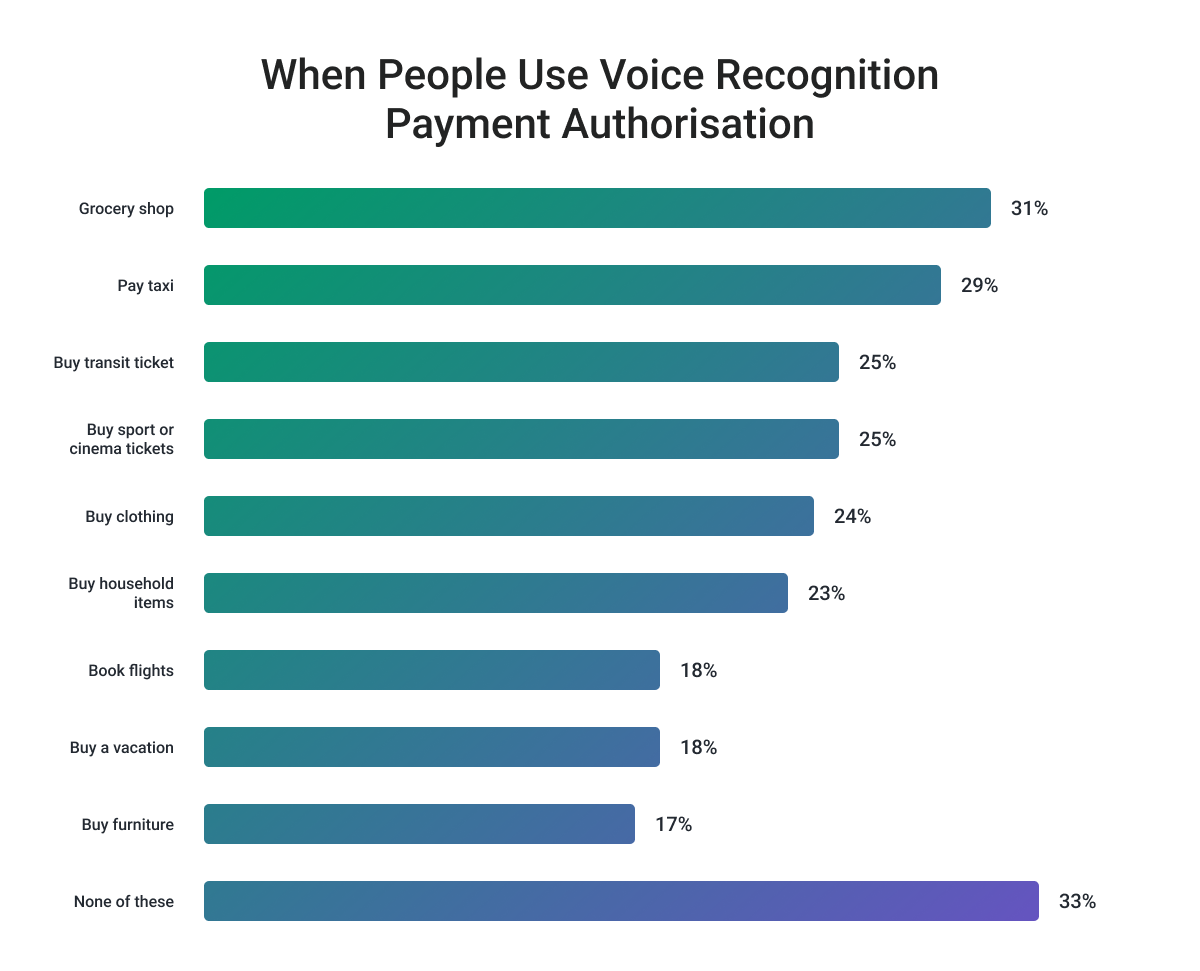
Voice-based payments take advantage of embedded payments by using the user's voice to authorize a payment. The unique vocal characteristics of the user are analyzed to verify their identity, adding an extra layer of security to every transaction, especially for large corporate ones.
Ajay Bhalla, President of Cyber & Intelligence at Mastercard, said, "Voice biometrics provide an additional level of security and convenience to our customers. It is a great example of how we are leveraging technology to enhance the authentication process and make payments more seamless and secure."
Financial institutions implementing voice payments also must adhere to strict data protection and privacy regulations to ensure the security and confidentiality of user information. This makes voice technology much safer to use on a daily basis, compared to traditional PIN numbers or complex passwords..png)
Security Concerns Regarding Voice Authentication
While voice authentication in finance offers the potential for enhanced security and convenience, it's important to recognize that it is not foolproof. Many factors can affect the accuracy of voice recognition systems, while hacking and regulations are other concerns. Here are some common challenges regarding voice authentication:
1. Regulatory Considerations
Fintech companies implementing voice authentication need to adhere to applicable data protection and privacy regulations. They must ensure the secure storage and handling of voiceprints to protect users' personal information.
Voice authentication is gaining traction in the fintech industry due to its convenience, security benefits, and potential for improving the customer experience. However, it is essential to note that it is just one component of a comprehensive security strategy and is often used in conjunction with other authentication methods for enhanced security.
2. Customer Frustration
Some users have reported instances of failed authentication due to background noise, changes in their vocal tone, or even a simple cold affecting their voice. This unreliability has led to prolonged authentication processes, leaving customers exasperated and questioning the touted benefits of the technology.
Ambient noise during the authentication process can play a big role in failed authentication due to distortions and it often affects the accuracy of the match. Some people can only use this technology when they are at home or in a silent office, but for those who want to use it outside or in traffic, there may be issues with authentication.
Another problem can be the device the user is using. If they have a device with a highly sensitive microphone, it will capture even more noise making it almost impossible to authorize payments or log in.
An additional layer of frustration arises from the stark disparity between customers with strong accents and those who speak languages devoid of intricate inflections. Voice authentication systems often struggle to accurately capture and interpret the nuances of various accents, leading to repeated failed verification attempts for individuals with non-standard speech patterns.
3. Data Privacy & Hackers
With a lot of hackers targeting banks and financial institutions, many institutions have legitimate concerns about the security of voice biometric data. Breaches and unauthorized access can lead to further resistance against adopting this type of authentication since protecting data can be expensive.
Some customers might have concerns about the security of their voice data. They may worry about the storage and potential misuse of their biometric information, especially if they are unfamiliar with the technology's security measures. One of the most secure ways to protect sensitive biometric data is by using encryption.
Data should be encrypted both during transmission and while at rest in storage. Strong encryption protocols ensure that even if data is intercepted or compromised, it remains unreadable without the proper decryption keys. Also, banks and financial institutions should have well-defined data breach response plans in place. Quick and transparent communication with affected users is crucial in case of a breach.
False positives in the context of voice authentication happen when a system incorrectly identifies an individual as an authorized user by giving it access to all financial data. This is a big concern as AI tools are becoming more sophisticated in cloning voice and creating models able to get through authentication and get access to a variety of accounts.
4. Integration with Existing Systems
Integration of voice authentication with other systems involves combining voice recognition technology with existing software, applications, and platforms to enable seamless and secure authentication and access control.
The current ways to integrate voice authentication are:
Application Programming Interfaces (APIs). Voice authentication providers often offer APIs that allow developers to incorporate voice recognition capabilities into their applications, platforms, or services. APIs provide a standardized way for different systems to communicate and exchange data.
Software Development Kits (SDKs). Voice authentication SDKs provide pre-built libraries, tools, and resources that developers can use to integrate voice recognition functionalities into their applications. SDKs simplify the integration process and speed up development.
Custom Solutions. Organizations can develop custom solutions by integrating voice authentication technology directly into their existing authentication systems, mobile apps, websites, or backend systems. With multi-factor authentication (MFA) voice authentication can be integrated as an additional layer of security in multi-factor authentication setups. This could involve combining voice authentication with other factors like passwords, fingerprints, or facial recognition.
Single Sign-on. Voice authentication can also be integrated with single sign-on solutions, allowing users to access multiple applications or services with a single voice-based authentication process. Successfully integrating voice authentication requires a solid understanding of the technology and the existing systems it will be integrated with and solid collaboration between development teams, IT departments, and security experts to ensure a smooth integration process.
What are the Benefits of Voice Authentication?
The benefits of biometric authentication include efficiency, easy user interface, reduced administrative costs, and more seamless payment transactions. Machine learning and AI will enhance the biometric authentication methods currently in place, with research currently being conducted into gait analysis, palm vein scanning, wearable biometric devices, payment cards that include biometric sensors, and blockchain-based biometric payments.
Minimized Risk of Fraud
Voice authentication provides an additional layer of security by verifying the unique vocal characteristics of individuals, making it harder for fraudsters to impersonate or gain unauthorized access. This reduces the risk of fraudulent activities such as identity theft and unauthorized transactions, enhancing overall account security for customers. However, with the rise of AI, new potential for fraudsters to trick this technology is likely to emerge.
Improved KYC (Know Your Customer)
By accurately verifying customers' identities through their voiceprints, banks can ensure compliance with regulatory requirements and mitigate the risk of fraudulent account openings. This streamlined and reliable KYC process helps establish trust and transparency in customer relationships.
Easy User Interface
Voice authentication offers a user-friendly interface that simplifies the authentication process. Many people have grown used to using Alexa, Siri, and Google Assistant, meaning most financial app users will likely have an easy time adopting new voice technology. Just by speaking a passphrase or providing a voice sample, users can eliminate the need to remember complex passwords or carry physical authentication devices.
Reduced Administrative Costs
Voice authentication tech can contribute to reducing administrative costs for banks by automating the authentication process and live customer service. Compared to traditional methods such as manual identity verification or physical token distribution, voice authentication could potentially eliminate the need for additional resources and infrastructure.
New Features that Retain Customers
With advancements in machine learning and AI, research is being conducted on various biometric authentication methods, such as gait analysis, palm vein scanning, wearable biometric devices, and biometric-enabled payment cards. Some of these cutting-edge technologies provide new opportunities to create personalized and secure banking experiences that many users enjoy.
Voice authentication offers several advantages as it is convenient for users as they can authenticate themselves using their voice without the need for additional hardware or tokens. It also helps in reducing operational costs for financial institutions by replacing traditional authentication methods like passwords or PINs.
Voice Authentication Use Cases: Fintech, Events & Ticketing, Media and Entertainment
In today's digital age, safeguarding user data and ensuring secure transactions have become paramount in various industries. One such technology that has gained significant traction is voice authentication. By using unique voice characteristics as a biometric identifier, voice authentication provides an additional layer of security to verify users' identities before granting access to sensitive information.
In this part, we will explore the applications of voice authentication in three distinct industries: fintech, events & ticketing, and media & entertainment. Each of these sectors relies heavily on secure transactions and user verification, making them ideal candidates for the implementation of voice authentication technology. We will dive into specific use cases within each industry, highlighting the benefits and challenges associated with integrating voice authentication into the processes of each industry.
Fintech
Mobile Banking: Speak Your Way to Secure Finances
Mobile banking has revolutionized the way people manage their finances, allowing users to access their accounts, transfer funds, and make payments through their smartphones. With the increasing number of mobile banking users, ensuring the security of financial transactions has become a top priority for banks and financial institutions.
Voice authentication in mobile banking apps provides an additional layer of security, making it more difficult for cybercriminals to gain unauthorized access to users' accounts. By using unique voice characteristics as a biometric identifier, voice authentication verifies the user's identity before granting access to sensitive financial information.
The advantages of using voice authentication in mobile banking include enhanced security, reduced risk of identity theft, and improved user experience. However, there are challenges, such as potential false rejections, privacy concerns, and the need for continuous improvement in voice recognition technology.
Online Trading Platforms: A Safer Way to Invest
Online trading platforms have become increasingly popular, enabling individual investors to trade stocks, bonds, and other financial instruments with just a few clicks. As these platforms handle large volumes of financial transactions daily, ensuring the security of user accounts and transactions is crucial.
Implementing voice authentication in online trading platforms can provide an added layer of security by verifying users' identities before allowing them to execute trades. This helps protect investors from unauthorized transactions and reduces the risk of fraud.
The benefits of incorporating voice authentication into online trading platforms include increased security, more user-friendly verification processes, and reduced likelihood of unauthorized access. Potential drawbacks include technical challenges, privacy concerns, and the possibility of user frustration if the technology fails to recognize their voice accurately.
Peer-to-Peer Payments: The Future of Secure Transactions
Peer-to-peer (P2P) payment platforms have simplified the process of transferring money between individuals, making it easy to split bills, pay friends, or settle debts. As the popularity of these platforms grows, so does the need for robust security measures to protect users from fraud and unauthorized access. Voice authentication can play a significant role in securing P2P transactions by confirming users' identities before allowing them to send or receive funds. By utilizing voice biometrics, these platforms can offer a seamless and secure user experience while minimizing the risk of fraud. Ensuring the security and user convenience of P2P transactions is essential for maintaining trust in these platforms. Voice authentication offers a unique solution that balances the need for robust security measures with the demand for a frictionless user experience.
Customer Support: Reinventing Security and Satisfaction
Customer support is a critical aspect of the fintech industry, as it directly affects customer satisfaction and loyalty. Banks and financial institutions must provide a secure and efficient customer support experience while protecting sensitive customer information.
Integrating voice authentication into customer service calls can help verify the caller's identity and streamline the support process. By confirming the caller's identity using their unique voice characteristics, support agents can quickly access relevant customer information without requiring lengthy verification procedures. Improving customer satisfaction and security through voice authentication in customer support calls not only enhances the overall customer experience but also reduces the risk of fraud and unauthorized access to customer data.
Events & Ticketing
Ticket Purchases: Goodbye to Fraud?
The process of purchasing tickets for events, concerts, and sports games has largely moved online, providing a convenient and efficient way for consumers to secure their spots. However, this shift to digital platforms has also opened the door for fraudsters to exploit vulnerabilities and engage in illicit activities like ticket scalping and counterfeit ticket sales.
Integrating voice authentication into the ticket-purchasing process can help mitigate these risks by ensuring that the buyer's identity is verified before the transaction is completed. This added layer of security not only reduces the likelihood of fraudulent transactions but also improves the overall user experience by streamlining the ticket-purchasing process.
Event Check-in: The Future of Seamless Entry
At large-scale events, efficient check-in procedures are essential for ensuring smooth operations and a positive experience for attendees. Traditional check-in methods, such as scanning physical tickets or checking names on a guest list, can be time-consuming and error-prone. Implementing voice authentication for event check-ins can significantly improve the efficiency of the process by allowing attendees to confirm their identities using their unique voice characteristics. This technology can expedite the check-in process, reduce wait times, and minimize the risk of unauthorized entry.
VIP Access: Exclusivity Amplified
For exclusive events and VIP areas, maintaining strict access control is vital to ensure a premium experience for high-profile guests. Traditional access control methods, such as wristbands or physical badges, can be easily lost, stolen, or counterfeited, compromising the security and exclusivity of the event.
Voice authentication offers a more secure and reliable solution for managing VIP access. By utilizing the guests' unique voice biometrics to verify their identity, event organizers can maintain a higher level of security and exclusivity while providing a seamless and convenient experience for VIP guests.
The integration of voice authentication in the events and ticketing industry offers several key benefits, including improved security, streamlined processes, and enhanced user experiences. As the technology continues to advance and gain widespread adoption, it's likely that more event organizers will embrace voice authentication as a standard practice for managing access and ticket sales.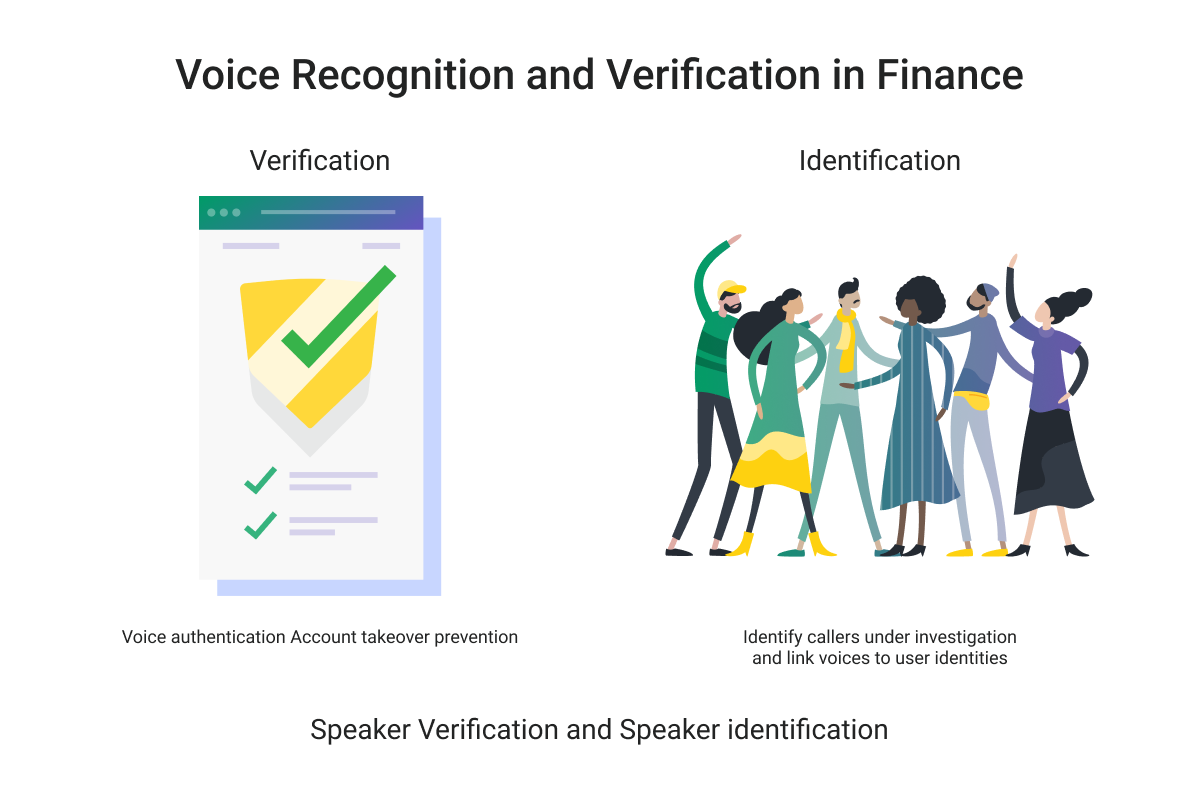
Media and Entertainment
Streaming Services: Personalization Meets Privacy
The rise of streaming services like Netflix, Hulu, and Spotify has revolutionized the way people consume media, by offering personalized and on-demand content. As these platforms handle sensitive user data and provide tailored recommendations, ensuring secure access to user profiles is crucial.
Implementing voice authentication for user profiles on streaming services can enhance security and privacy by verifying users' identities based on their unique voice characteristics. This helps protect user accounts from unauthorized access and provides a more personalized experience by allowing users to switch profiles quickly and easily.
Gaming Platforms: Leveling Up Security
Online gaming platforms, such as Steam, Xbox Live, and PlayStation Network, have become increasingly popular as they provide gamers with access to a vast array of digital games and interactive experiences. With the growing number of users and the potential for in-game purchases, securing user accounts and transactions is of the utmost importance.
Voice authentication can be integrated into gaming platforms to provide a secure and user-friendly experience. By using voice biometrics to verify users' identities, gaming platforms can reduce the risk of account hijacking and fraud, ensuring a safe environment for gamers to enjoy their favorite titles.
Smart TVs and Devices: The Future of Personalized Entertainment
Smart TVs and devices, such as Amazon's Fire TV and Google's Chromecast, have transformed the way we consume media, offering users the ability to stream content from various sources directly to their television screens. Since these devices often store sensitive user information and enable access to multiple streaming services, ensuring users have a secure and personalized experience is essential.
Voice authentication can be integrated into smart TVs and devices to provide a more secure and convenient way for users to access their content. By verifying users' identities based on their unique voice characteristics, these devices can offer personalized recommendations and settings while maintaining a high level of security and privacy.
The media and entertainment industry stands to benefit significantly from the integration of voice authentication technology. By providing a secure and personalized experience for users across streaming services, gaming platforms, and smart devices, voice authentication can help protect sensitive user data and improve overall user satisfaction. As the technology continues to evolve, it's likely that we'll see even more innovative applications of voice authentication within the media and entertainment sector.
The Biggest Companies That Benefit from Voice Authentication
Amazon: Amazon's virtual assistant, Alexa, uses voice recognition for user authentication and personalized experiences. Amazon Echo devices allow users to perform tasks and access information using voice commands.
Apple: Apple's Siri voice assistant utilizes voice recognition for user interactions, and the company has implemented voice authentication for unlocking devices and authorizing transactions using the "Hey Siri" feature.
Google: Google's Voice Match technology enables voice authentication for accessing devices and personalized services. Google Assistant also uses voice recognition for user interactions by using the phrase "Hey, Google".
Microsoft: Microsoft's Cortana virtual assistant employs voice recognition for user interactions and authentication. Additionally, Microsoft Azure offers voice authentication tools for businesses. Samsung: Samsung devices, including smartphones, smart TVs, and innovative home products, utilize voice recognition for user authentication and device control.
Wells Fargo: Wells Fargo, a major financial institution, introduced voice authentication for mobile banking. Customers can securely access their accounts and perform transactions using their voice prints.
Barclays: Barclays, a multinational bank, introduced voice recognition for customer authentication in its mobile banking app. Customers can use their voices to log in to their accounts. A staggering 93% of Barclays customers have reported increased satisfaction with the voice recognition system because it has significantly reduced transaction time.
HSBC: HSBC also implemented voice authentication for customer convenience and security in its phone banking services. HSBC saw a big decrease in banking fraud since it started using voice recognition technology.
Final Word
In the realm of digital identity protection, voice recognition tech has emerged as a transformative force. Its integration into everyday devices has moved voice authentication from science fiction to reality for thousands of people, with the global market projected to grow. Financial institutions and fintechs are using its potential to increase security. Softjourn is devoted to providing software development services for fintech, banks, and other financial institutions as our experts understand the regulations and the latest technologies used in finance.
Of course, there are obstacles to keep in mind, including accuracy concerns, data safety, customer adoption, and regulatory compliance. As the technology becomes more sophisticated and gains broader acceptance, voice payments are expected to play a more significant role in shaping the future of financial transactions.











