APIs are the backbone of modern business operations, connecting applications, enabling partner integrations, and powering the data exchanges that drive digital transformation. But this connectivity comes with significant risk.
83% of web traffic is API-related, making them prime targets for cyberattacks. The business impact of API vulnerabilities extends far beyond IT infrastructure and can affect customer trust, regulatory compliance, and competitive positioning.
Understanding API security risks is a strategic imperative for business leaders, not just a technical concern.
This guide examines the critical API security risks and vulnerabilities facing organizations today and provides actionable mitigation strategies for executives who must balance innovation with security.

What is API Security?
Defining API Security in Business Terms
API security refers to the practices, technologies, and policies that protect Application Programming Interfaces from unauthorized access, data breaches, and malicious attacks.
Unlike traditional web applications where users interact through browsers, APIs facilitate machine-to-machine communication, automatically exchanging data between systems without human oversight. This fundamental difference creates unique security challenges.
When you secure an API, you're protecting the data it transmits, controlling who can access it, and ensuring that only authorized actions can be performed. Think of APIs as the digital doorways into your systems. Without proper security, these doorways can be exploited to access customer data, manipulate business processes, or disrupt operations.
A secure API validates every request, enforces access controls, encrypts sensitive data, and maintains detailed logs of all activity.
The challenge is that APIs in cybersecurity operate differently from traditional applications. They process requests at a massive scale, often handling thousands or millions of transactions without direct human involvement.
APIs connect diverse systems, including internal applications, partner platforms, mobile apps, and third-party services, each with different security requirements.
And they evolve rapidly, with new versions and endpoints constantly being deployed to support business agility.

Why API Security Demands Executive Attention
API security has escalated from a technical implementation detail to a board-level concern for several compelling reasons:
Financial and Legal Liability: Data breaches through API vulnerabilities can result in millions of dollars in regulatory fines under GDPR, HIPAA, CCPA, and other frameworks.
API breaches can carry significant costs, with recent reports estimating average remediation costs around $591,400 per incident in the US, which can be even higher for some industries, such as financial services. A high percentage of organizations report experiencing API-related security incidents, with some studies indicating as many as 85% of organizations reporting an API incident in the past year.
Beyond fines, organizations face litigation costs, mandatory breach notifications, and credit monitoring services for affected customers.
Operational Continuity: APIs often control critical business functions: payment processing, inventory management, customer authentication, and supply chain coordination. When API security fails, it doesn't just expose data; it can halt revenue-generating operations. A compromised API might enable attackers to manipulate pricing, redirect transactions, or take systems offline entirely.
Reputation and Customer Trust: In an era where customers expect their data to be protected, API breaches make headlines and erode trust. The competitive disadvantage of a publicized security incident can persist for years, affecting customer acquisition costs, retention rates, and brand value.
Competitive Intelligence: APIs often expose business logic, data structures, and operational processes. Inadequate API security can leak strategic information to competitors or enable theft of proprietary algorithms and business methods.
Regulatory Scrutiny: Regulators increasingly view API security as a fundamental requirement, not an optional enhancement. Organizations must demonstrate robust API security controls during audits and compliance assessments across industries, from financial services to healthcare and e-commerce.
The API Security Threat Landscape
APIs have become the preferred target for cyberattacks. The reason is simple: they provide direct access to data and business logic, often with less security monitoring than traditional web applications.
Why attackers target APIs:
- Direct data access without navigating user interfaces
- High-value targets (customer data, financial transactions, business logic)
- Often less visible to security teams than web traffic
- Vulnerabilities can be exploited at machine speed
The sophistication of API attacks has evolved significantly, and API vulnerabilities experienced a 10% year-over-year increase across platforms.
Early threats involved basic authentication testing and simple injection attempts. Today's attackers use automated tools designed specifically to exploit API vulnerabilities, systematically probing for authorization flaws and configuration weaknesses.

Unique API security challenges:
Volume and complexity: Organizations typically manage hundreds or thousands of API endpoints, making comprehensive oversight difficult.
Rapid change: APIs evolve constantly as new features deploy, creating a moving security target.
Shadow APIs: Deprecated versions, test endpoints, and undocumented APIs often remain accessible without proper security controls. Attackers actively hunt for these overlooked entry points.
Machine-speed attacks: Without human intermediaries, attacks happen faster and at greater scale than traditional application threats.
These API threats aren't theoretical; instead, they represent active attack patterns that cybercriminals exploit daily. Understanding this landscape is critical context for the specific vulnerabilities we'll examine next.
Critical API Security Risks and Vulnerabilities
1. Broken Object Level Authorization (BOLA)
What it is: Broken Object Level Authorization occurs when APIs fail to verify that users have permission to access specific data objects. Attackers manipulate object identifiers—like user IDs or account numbers—to access other users' records. BOLA is the #1 API vulnerability according to OWASP.
Business impact: This API vulnerability enables systematic data theft at scale. Attackers can iterate through IDs to harvest entire databases of customer information, financial records, or proprietary business data. The breach may go undetected for months, affecting thousands or millions of records before discovery.
How it happens: Consider an API endpoint that returns customer order details: /api/orders/12345. If the API only checks that the user is authenticated but doesn't verify they own order 12345, an attacker can simply change the number to 12346, 12347, and so on—accessing every customer's order history. This pattern repeats across resources: user profiles, invoices, medical records, any data object with a predictable identifier.
Red flags to watch for: APIs that use sequential IDs in URLs or request bodies without explicit ownership validation. Lack of authorization checks beyond initial authentication. Missing audit logs for data access patterns.
How to Mitigate: Implement object-level authorization checks that verify the requesting user has explicit permission to access each specific resource, not just the endpoint generally.
2. Broken Authentication
What it is: Broken authentication includes weak credential management, insufficient session handling, and flawed token implementation—such as hardcoded API keys, tokens that never expire, lack of multi-factor authentication, and predictable passwords vulnerable to brute-force attacks.
Business impact: Compromised authentication provides attackers with legitimate access credentials, allowing them to operate as authorized users while bypassing security monitoring. This enables data exfiltration, unauthorized transactions, and privilege escalation. Because the attacker appears legitimate, detection becomes significantly more difficult.
How it happens: A mobile app developer hardcodes an API key directly in the application code for convenience. Attackers decompile the app, extract the key, and gain unrestricted API access. Or an API issues JWT tokens with no expiration date—once obtained through phishing or credential stuffing, these tokens provide permanent access even after password changes.
Red flags to watch for: API keys visible in client-side code or public repositories. Tokens without expiration policies. Absence of rate limiting on authentication endpoints. No account lockout after failed login attempts. Single-factor authentication for administrative functions.
How to Mitigate: Adopt OAuth 2.0 for API authentication best practices, implement short-lived tokens with refresh mechanisms, require MFA for privileged access, and never embed credentials in client applications.

3. Excessive Data Exposure
What it is: APIs return more data than necessary when they send complete data objects instead of filtering responses based on client needs and user authorization. Developers often rely on client-side filtering, incorrectly assuming clients will only display relevant fields.
Business impact: This API security issue leaks sensitive information including personally identifiable information (PII), internal system details, business logic, and data that competitors or attackers can exploit. The exposed data may violate privacy regulations, provide reconnaissance for additional attacks, or reveal strategic business information.
How it happens: An API endpoint designed to display a user's public profile returns the complete user object from the database, including email, phone number, date of birth, partial credit card numbers, and internal user flags. The web interface only displays the name and photo, but anyone inspecting API responses sees all fields. Attackers systematically harvest this exposed data for identity theft or social engineering.
Red flags to watch for: API responses containing fields that aren't displayed or used by the client. Sensitive data in error messages. Database objects returned directly without filtering. Generic endpoints that return different data based solely on URL parameters without field-level access control.
How to Mitigate: Design APIs to return only necessary fields for each use case, implement field-level authorization, and regularly audit API responses to ensure no sensitive data leakage.
4. Security Misconfiguration
What it is: Security misconfiguration happens when APIs are deployed with insecure default settings, unnecessary features enabled, verbose error messages, missing security headers, or outdated components with known vulnerabilities.
Business impact: [STAT: security misconfigurations contributed to X% of unprotected APIs]. Misconfigurations create easily exploitable vulnerabilities that attackers actively scan for using automated tools. They can expose sensitive system information, enable unauthorized access, or facilitate other attack types. The widespread nature of misconfiguration makes it a high-probability risk.
How it happens: A development team enables CORS (Cross-Origin Resource Sharing) to allow requests from any domain during testing, then forgets to restrict it before production deployment. Now any website can make requests to your API. Or detailed error messages meant for debugging remain active, revealing database structure, file paths, and software versions that attackers use to craft targeted exploits.
Red flags to watch for: Default administrative credentials unchanged. Unnecessary HTTP methods (PUT, DELETE) enabled on read-only resources. Stack traces or detailed errors returned to clients. Missing security headers (HSTS, CSP). Outdated framework versions with published CVEs.
How to Mitigate: Establish secure configuration baselines, automate configuration scanning in CI/CD pipelines, disable unnecessary features, and implement a rigorous patch management process for all API components and dependencies.
5. Lack of Rate Limiting and Resource Controls
What it is: APIs without proper rate limiting and resource controls allow unlimited requests from individual users or systems, making them vulnerable to Denial of Service (DoS) attacks and resource exhaustion.
Business impact: Service disruptions affect customer experience, damage reputation, and result in direct revenue loss during outages. Attackers can overwhelm systems to mask other malicious activities or extort organizations by threatening continued attacks. Even without malicious intent, poorly designed clients or bugs can accidentally consume excessive resources, degrading service for all users.
How it happens: An attacker discovers your product catalog API has no rate limiting. They write a script that makes thousands of requests per second, overwhelming your servers. Legitimate customers can't load product pages, directly impacting sales. Or an API allows users to request massive data exports with a single call, and an attacker repeatedly triggers these requests to exhaust database connections and storage.
Red flags to watch for: No request limits per user, IP address, or API key. APIs that allow arbitrarily large responses or complex queries without restrictions. Absence of request queuing or throttling. No monitoring for abnormal traffic patterns or spikes.
How to Mitigate: Implement comprehensive rate limiting based on user, IP address, and API key. Deploy load balancing and traffic distribution systems. Monitor for unusual traffic patterns and establish automated responses to suspicious activity. Design APIs with resource efficiency and define maximum payload sizes.

6. Injection Attacks
What it is: Injection attacks occur when APIs accept and execute untrusted data as commands or queries. Common types include SQL injection, command injection, and NoSQL injection—all exploiting insufficient input validation.
Business impact: Successful injection attacks can result in complete database compromise, unauthorized system access, data destruction, or service hijacking. Attackers can bypass authentication, extract entire databases, modify or delete records, or execute system commands with API privileges. These vulnerabilities often enable the most severe breaches.
How it happens: An API endpoint accepts a user ID parameter and directly inserts it into a SQL query without validation: SELECT * FROM users WHERE id=[user_input]. An attacker submits 1 OR 1=1 instead of a number, causing the query to return all user records. More sophisticated attacks can drop tables, create admin accounts, or execute operating system commands depending on database permissions.
Red flags to watch for: User input directly concatenated into database queries or system commands. Lack of input validation and sanitization. APIs accepting special characters without escaping. Error messages revealing query structure or database details.
How to Mitigate: Validate and sanitize all user inputs before processing. Use parameterized queries and prepared statements exclusively. Implement input type checking and allowlists for acceptable values. Apply principle of least privilege to database accounts used by APIs. Conduct regular penetration testing focused on injection vulnerabilities.
7. Improper Asset Management (Shadow APIs)
What it is: Improper asset management occurs when organizations lose track of their API inventory, resulting in undocumented, deprecated, or forgotten endpoints—often called "shadow APIs" or "zombie APIs"—that remain accessible without current security controls.
Business impact: These forgotten APIs represent significant API security challenges because they lack modern security measures while still providing access to production systems and data. Attackers specifically search for deprecated API versions or undocumented endpoints, knowing they're easier targets. Shadow APIs may use outdated authentication, have known vulnerabilities, or lack the monitoring applied to official APIs.
How it happens: Your team launches API v3 with improved security controls and migrates most clients. API v2 remains running for backward compatibility "temporarily" but never gets decommissioned. Two years later, v2 still runs with weaker authentication and known vulnerabilities. Attackers discover the old version through documentation archives or systematic probing and exploit its weaknesses to access current data.
Red flags to watch for: No comprehensive API inventory or documentation. Deprecated versions still accessible in production. Test or staging APIs exposed to the internet. APIs created by individual teams without central oversight. Inconsistent security controls across different API versions.
How to Mitigate: Maintain a comprehensive, current inventory of all APIs using automated discovery tools. Establish clear API lifecycle management processes with formal deprecation and decommissioning procedures. Monitor for unauthorized or unknown API endpoints. Implement API versioning policies with sunset dates and migration support.
8. Insufficient Logging and Monitoring
What it is: Insufficient logging and monitoring means APIs lack adequate visibility into security events, making it impossible to detect attacks in progress, investigate incidents, or prove compliance with regulatory requirements.
Business impact: Without proper logging, organizations remain blind to API threats. Attackers can operate undetected for months, maximizing damage. When breaches are eventually discovered, lack of logs complicates forensic investigation, making it difficult to determine scope, notify affected parties accurately, or prevent recurrence. Regulatory frameworks increasingly require security logging, making insufficient monitoring a compliance violation.
How it happens: An API logs only successful transactions for business analytics but doesn't record failed authentication attempts, authorization failures, or unusual access patterns. Attackers probe the API for vulnerabilities, systematically testing authorization on thousands of objects. Because failures aren't logged, security teams have no visibility into the reconnaissance activity. The attack succeeds without triggering any alerts.
Red flags to watch for: Logs stored only locally on API servers without centralization. No logging of authentication failures or authorization decisions. Absence of real-time alerting for suspicious patterns. Logs that don't capture sufficient detail (IP addresses, user agents, request parameters). No log retention policy or logs regularly deleted.
How to Mitigate: Implement comprehensive logging across all API interactions including authentication attempts, authorization decisions, data access, and errors. Centralize logs in secure, tamper-proof systems with appropriate retention. Deploy real-time monitoring and alerting for suspicious patterns. Integrate with SIEM platforms. Define and test incident response procedures.
9. Third-Party Integration Risks
What it is: Third-party integration risks arise when organizations connect to external APIs or allow third parties to access their APIs without adequate security vetting, monitoring, or access controls.
Business impact: Third-party vulnerabilities can compromise your entire API integration security posture through supply chain attacks. A security flaw in a partner's API can become an entry point to your systems, bypassing your direct security controls. Data shared with third parties may be exposed through their inadequate security. Additionally, excessive permissions granted to third-party integrations create unnecessary risk if those credentials are compromised.
How it happens: Your application integrates with a third-party payment processor's API. The processor suffers a breach, and attackers obtain API credentials for all integrated merchants. Because your integration uses overly permissive credentials, attackers can access customer data beyond what's needed for payment processing. Or a trusted business partner's API lacks proper input validation, allowing attackers to inject malicious data that flows through to your systems.
Red flags to watch for: No security assessment process for third-party APIs. Third-party integrations granted broad permissions beyond actual needs. Lack of monitoring for third-party API behavior changes. No contractual security requirements with vendors. Absence of contingency plans for third-party security incidents. Treating third-party data as inherently trustworthy.
How to Mitigate: Conduct thorough security assessments before integrating third-party APIs. Implement strict access controls limiting third-party API connections to minimum necessary permissions. Monitor third-party API behavior for anomalies. Establish contractual security requirements with vendors. Apply the same input validation to third-party data as user-submitted data. Maintain inventory of all external dependencies with security posture tracking.

10. Insecure Data Transmission
What it is: Insecure data transmission occurs when APIs use weak encryption, transmit sensitive data over unencrypted channels, or mishandle encryption keys—exposing data to interception and tampering.
Business impact: Regulatory frameworks increasingly mandate strong encryption for data in transit. Failures result in compliance violations, data breaches, and loss of customer trust. Even minor encryption weaknesses can have catastrophic consequences—exposed customer data, intercepted financial transactions, or stolen authentication credentials. The reputational damage from preventable encryption failures can be particularly severe.
How it happens: An internal API transmits employee data between microservices using plain HTTP instead of HTTPS, assuming the internal network is secure. An attacker who compromises a single server on that network can now intercept all API traffic, harvesting credentials and sensitive data. Or an API uses HTTPS but accepts outdated TLS 1.0 connections with weak cipher suites that attackers can break using known vulnerabilities.
Red flags to watch for: APIs accessible via HTTP instead of HTTPS. Support for outdated TLS versions (1.0, 1.1). Weak cipher suites enabled. Sensitive data transmitted in URL parameters (visible in logs). API keys or tokens sent in plain text. Missing certificate validation. Encryption keys stored alongside encrypted data.
How to Mitigate: Enforce HTTPS with current TLS versions (1.2 minimum, 1.3 preferred) for all API data security. Implement field-level encryption for highly sensitive data at rest. Use strong, current encryption algorithms (AES-256). Establish secure key management practices with proper rotation. Regularly update encryption protocols and disable deprecated versions. Never transmit sensitive data in URLs or headers where it may be logged.
How to Mitigate API Security Risks: A Strategic Framework
Addressing API vulnerabilities requires a comprehensive organizational approach, not just technical solutions. Here's a strategic framework for business and technology leaders to secure APIs effectively.
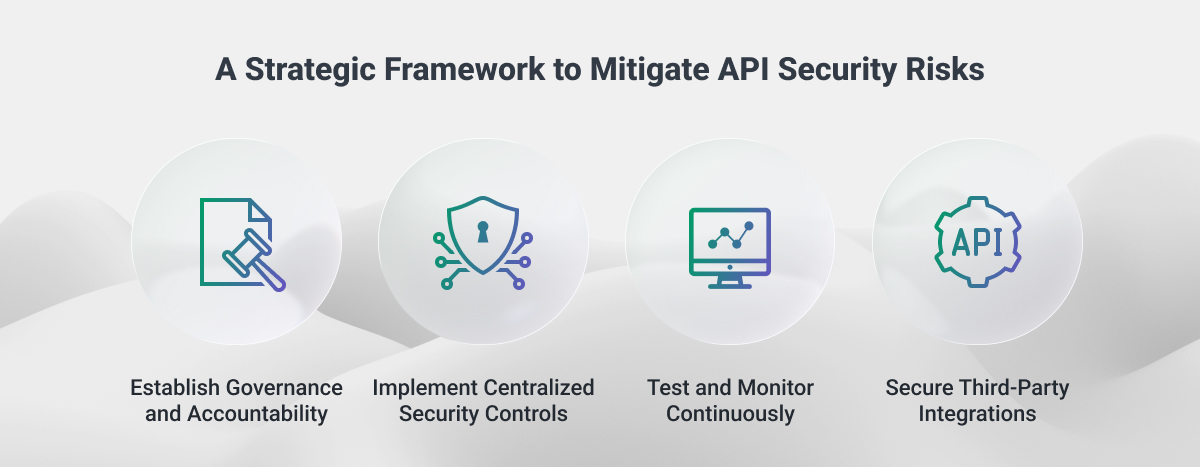
Establish Governance and Accountability
Start by designating clear executive ownership for API security. This leader coordinates between security, development, operations, and business teams to ensure consistent standards and priorities.
Create organization-wide API security policies that define mandatory requirements for all APIs. Maintain a centralized inventory of every API—who owns it, what data it handles, and its current security status. Regular governance reviews ensure new APIs meet security standards before deployment and existing APIs undergo periodic assessments.
Implement Centralized Security Controls
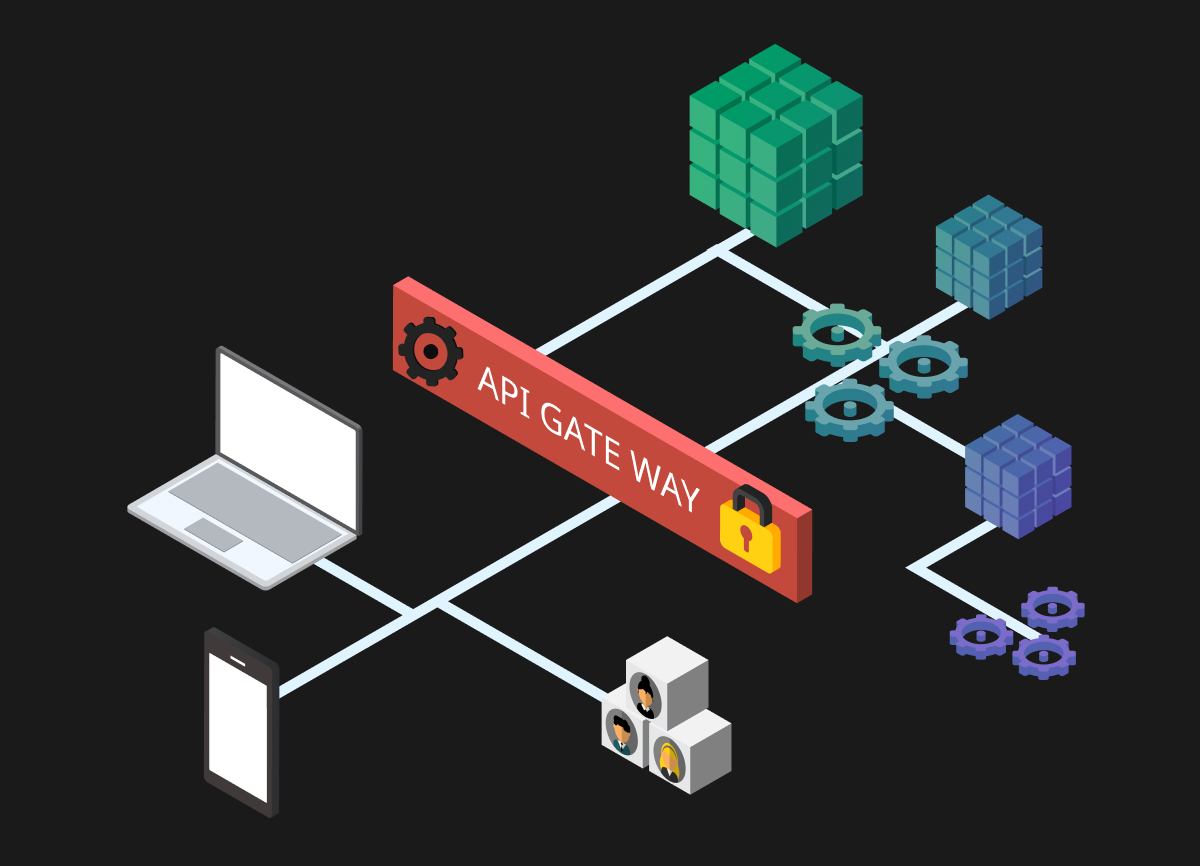
Deploy an API gateway to centralize security enforcement. Rather than each API implementing its own security, the gateway provides a single control point for authentication, access control, request validation, rate limiting, and monitoring. This approach ensures consistent protection and simplifies management.
Adopt industry-standard authentication frameworks rather than building custom solutions. Use strong encryption for all API communication. Apply "zero trust" principles—verify every request, trust nothing by default, and enforce least-privilege access.
Test and Monitor Continuously
Integrate security testing throughout your development process, not just at the end. Use automated tools to scan for vulnerabilities before APIs reach production.
Implement real-time monitoring to detect attacks as they happen. Establish clear incident response procedures so teams know exactly what to do when security issues arise.
Secure Third-Party Integrations
Evaluate the security practices of any third-party APIs you integrate with. Establish contractual security requirements with vendors. Grant third parties only the minimum access they need to function. Monitor their API behavior and maintain backup plans if a partner experiences a security incident.
Treat data from third-party sources with appropriate skepticism—validate it the same way you would validate data directly from users.
Building Your API Security Roadmap
Implementing comprehensive API security is a journey, not a one-time project. Organizations should approach it in phases, balancing quick wins with strategic long-term improvements. A phased roadmap allows you to address critical vulnerabilities immediately while building toward mature security practices over time.
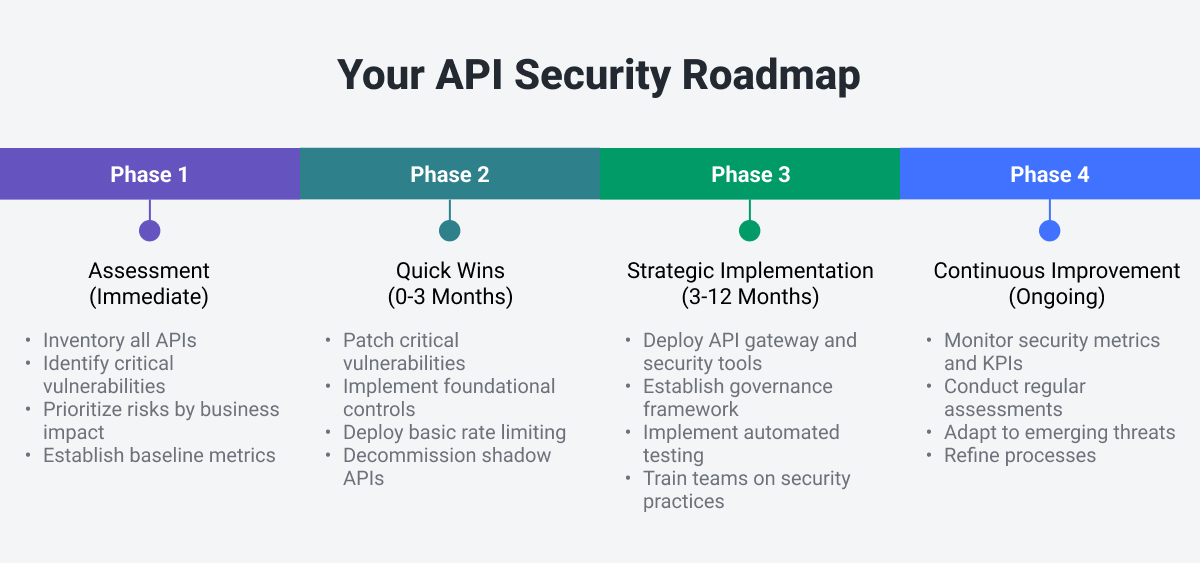
API Security Tools and Solutions
Protecting APIs requires a combination of specialized tools and platforms. Understanding the categories of API security solutions helps organizations make informed decisions about building their security stack.
API Gateways serve as the foundation, providing centralized authentication, authorization, rate limiting, and traffic management. They act as a single enforcement point for security policies across all APIs.
API Security Testing Tools identify vulnerabilities during development and in production environments. These include static analysis tools that scan code, dynamic testing tools that probe running APIs, and specialized scanners designed specifically for API vulnerabilities like BOLA and injection flaws.
API Discovery and Inventory Tools automatically identify all APIs in your environment—including shadow APIs that may exist outside formal documentation. This visibility is critical for comprehensive security management.
API Monitoring and Threat Detection Platforms analyze API traffic in real-time, using behavioral analysis and machine learning to detect anomalous patterns, credential abuse, and attack attempts. These tools integrate with SIEM platforms for comprehensive security operations.
Cloud API Security solutions are particularly important for organizations using cloud-native architectures. Cloud providers offer native security services including web application firewalls, DDoS protection, and identity management that integrate seamlessly with cloud-based APIs.

When selecting API security tools, prioritize solutions that integrate with your existing infrastructure, provide comprehensive visibility, and scale with your API growth. Consider whether to build custom solutions or adopt commercial platforms based on your team's expertise and resources.
Conclusion
API security risks directly threaten your revenue, customer trust, and regulatory compliance. The vulnerabilities outlined in this guide are actively exploited by attackers today.
Securing APIs requires executive commitment, clear governance, and comprehensive technical controls. The cost of inaction far exceeds the investment in proper protection.
The time to act is now – before vulnerabilities become breaches.
Looking to strengthen your API security posture? Our team specializes in secure API integration services, helping businesses implement robust protection while enabling digital transformation. Learn more about our API integration services and get in touch.
Frequently Asked Questions
What are the most common API security risks?
The most prevalent API security risks include Broken Object Level Authorization (BOLA), broken authentication, excessive data exposure, security misconfiguration, lack of rate limiting, injection attacks, improper asset management (shadow APIs), insufficient logging, third-party integration risks, and insecure data transmission. BOLA consistently ranks as the #1 API vulnerability, allowing attackers to access unauthorized data by manipulating object identifiers.
How do API security challenges differ from web application security?
API security faces unique challenges compared to traditional web application security. APIs handle machine-to-machine communication at massive scale without human oversight, making attacks faster and harder to detect. They lack visual interfaces that help identify security issues, often expose broader data and functionality, and change more frequently. APIs also typically use token-based authentication rather than session-based methods, requiring different security approaches.
What is the first step in securing our APIs?
Start with a comprehensive API risk assessment. Inventory all your APIs—including internal, external, partner, and third-party integrations. Identify which APIs handle sensitive data or critical business functions. This visibility is fundamental to understanding your exposure and prioritizing security investments. Many organizations discover "shadow APIs" during this process—undocumented endpoints that lack proper security controls.
What is broken object level authorization (BOLA)?
Broken Object Level Authorization occurs when APIs fail to verify that users have permission to access specific data objects. Attackers exploit this by changing object identifiers in requests (like user IDs or account numbers) to access other users' data. BOLA is the #1 API security risk because it enables systematic data theft at scale. Proper mitigation requires implementing authorization checks that verify users can access each specific resource, not just the endpoint generally.
How often should we conduct API security assessments?
Conduct comprehensive API security assessments quarterly at minimum, with annual penetration testing by qualified professionals. Additionally, perform security testing for every new API before production deployment and whenever significant changes occur to existing APIs. Implement continuous automated scanning to detect vulnerabilities between formal assessments. Given how rapidly APIs evolve and new threats emerge, ongoing vigilance is essential for maintaining security posture.
What role does an API gateway play in security?
An API gateway serves as a centralized security control point for all API traffic. Following API gateway best practices, it enforces authentication and authorization, implements rate limiting to prevent abuse, validates and sanitizes inputs, maintains comprehensive logs, and detects threats in real-time. Rather than each API implementing security independently, the gateway provides consistent protection across your entire API ecosystem, simplifying management and reducing the risk of configuration errors.
How do we secure third-party API integrations?
Securing third-party API integrations requires a multi-faceted approach. Conduct security assessments before integrating any external API, evaluating their authentication methods, encryption standards, and incident response capabilities. Establish contractual security requirements with vendors. Apply the principle of least privilege—grant only minimum necessary access. Validate and sanitize all data from third-party sources just as you would user input. Monitor third-party API behavior for anomalies and maintain contingency plans for security incidents.
What compliance standards apply to API security?
API compliance requirements vary by industry and geography. Common standards include GDPR for data privacy (EU), HIPAA for healthcare data (US), PCI DSS for payment processing, SOC 2 for service organizations, and CCPA for California consumer data. Many frameworks like ISO 27001 and NIST Cybersecurity Framework include API security requirements. Organizations should also follow OWASP API Security Top 10 as a baseline. Consult with legal and compliance teams to identify specific requirements for your industry and markets.







